What Is Credential Stuffing?
Credential stuffing is an automated account takeover (ATO) attack in which compromised usernames and passwords are leveraged to gain unauthorized access to user accounts.
Credential stuffing is typically perpetrated with automated tools like bots or scripts that attempt to gain access to accounts by testing multiple credential combinations until they find a match. Thanks to a rising number of phishing scams and an endless stream of data breaches, fraudsters can purchase large volumes of credentials through dark web marketplaces.
Once they’ve gained access to an account, these cybercriminals are free to make unauthorized purchases using stolen or card-on-file payment details, transfer money out of checking and savings accounts, or pilfer sensitive corporate or personal data.
This can also be a stepping stone to hijacking the user’s other accounts or systems. It doesn’t help that many of us tend to use easily deduced variations of the same 10 passwords for banking, retail, utilities, social media, workplace applications, and everything in between.
The losses from successful ATOs in 2021 is estimated at over $12 billion. But destroyed reputations and lost customer trust can cost billions more. Credentials stuffing enables cybercriminal organizations to automate this crime at scale.
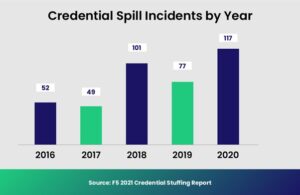
“In 2020, there were 193 billion credential stuffing attacks globally, with 3.4 billion hitting financial services organization specifically.”

Credential Stuffing: A Closer Look
Here’s how credential stuffing works:
Step 1: Cybercriminal organizations harvest or acquire mass lists of stolen usernames and passwords. These lists are sold on the dark web or traded in underground forums.
Step 2: The stolen credentials are added to a botnet, a network of infected computers that the hacker can control remotely. The botnet automates the process of trying different username and password combinations at high velocities. Due to rampant password re-use, credentials stuffing attacks simultaneously test these login combinations across dozens or even hundreds of different sites.
Step 3: If a login is successful on any one of these sites, the fraudster gains access to that account. And if the login credentials are the same for other accounts belonging to the user, they could quickly fall into the hands of the attackers.
Step 4: The attacker is also free to use the account to commit various types of fraud, such as buying items with a stolen credit card, applying for loans, selling counterfeit goods, draining banking accounts, and more.
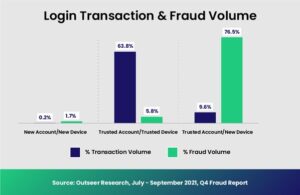
Financial services and online merchants in particular have found themselves under continuous attack from the kind of compromised accounts credential stuffing affords fraudsters. During the third quarter of 2021, for instance, Outseer saw that 71.9% of e-commerce fraud and 76.5% of digital banking fraud was committed through trusted user accounts accessed on a new device.
Credential Stuffing vs. Brute Force Attacks
Credential stuffing is often confused with brute force attacks. However, there are key differences between the two.
In the brute force attack, a fraudster tries to guess passwords or PINs by trying every possible combination until they find the correct one. Brute force attacks can be very time-consuming and often require a lot of computing power.
Credential stuffing, on the other hand, is far more efficient. This is because credential stuffing attackers use lists of stolen usernames and passwords that are readily available on the dark web. All the attacker has to do is to upload stolen credentials to a botnet, and the botnet will do the rest.
Another key difference is that brute force attacks attempt to try multiple username and password combinations against one or a handful of accounts, while credential stuffing attacks target known user login combinations against numerous websites.
Protection From Credential Stuffing for Individuals
Protection from credential stuffing is much easier for individuals than it is for organizations.
One of the most effective protection tactics for individuals is using different passwords for different accounts and changing them often. Using a password manager can help track all the different passwords without hassle. This may seem like a lot of work, but having all of your accounts secured is definitely worth it.
Another tactic individuals can use is enable two-factor authentication (2FA). This means that in addition to the account password, a user must input a one-time code sent to his device. 2FA makes it much harder (though not impossible) for attackers to access an account, even if they have the password.
Individuals should also be careful about the personal information they share online. Attackers often analyze their targets’ personal information on social media to guess their passwords or answer security questions.
Finally, being suspicious of any email or text message asking you to click through to a website to input a password or other sensitive information is a must. These are often phishing scams and can expose accounts to hackers.
Protection From Credential Stuffing for Organizations
Introducing protective measures against these attacks can be tricky for card issuers, banks, payment processors, or merchants. Striking the right balance between security and customer experience can be as difficult as it is critical—especially at a time when legitimate users may bail after just 30 seconds of added friction.
The most effective course of action is to employ detection and prevention tools that can differentiate between legitimate users and credential stuffing attacks. Outseer’s own account monitoring solution, for instance, defeats both fraudulent access and user friction at the same time.
Through identity science, predictive analytics, and strong authentication options such as FIDO compliant biometrics and passwordless authentication methods, we seamlessly distinguish between authentic users and intruders.
Unlike CAPTCHA checks, our frictionless fraud detection provides a fast, friendly user experience while kicking credential stuffing and other fraud attacks to the curb. By preventing 95% of all fraud loss with intervention rates as low as 5%, we deliver the best protection in the industry.
Stopping Credential Stuffing But Not Legitimate Users
Effective protection against credential stuffing is possible when combining advanced security solutions along with employee awareness. Organizations should make sure employees understand the risks of credential stuffing attacks and are trained to spot phishing scams and other social engineering-based attacks that could expose their login credentials.
Deploying the right tools and training can be a big win for everybody but the bad guys. To learn how you can protect against credential stuffing attacks and other forms of ATO fraud, schedule a free demo today.