In today’s ever-changing cyber threat landscape, ransomware groups are responsible for some of the most sophisticated and dangerous attacks on large organizations worldwide. Whether driven by financial gain or political motives (hacktivism), these gangs operate globally and often extort significant sums from their victims. They infiltrate systems, encrypt sensitive data, and demand ransom in exchange for a decryption key. If the ransom is unpaid, they threaten to release the stolen data publicly.
Among these groups, Lockbit has emerged as the most prominent, responsible for nearly 2,000 attacks since its formation in 2019.

Lockbit Overview
Lockbit, also known as “ABCD Ransomware,” is currently one of the most prolific ransomware groups. First observed in September 2019, it is known for blocking user access to systems and demanding ransom payments. Lockbit’s attacks span various platforms, including Windows and Linux, with victims across the U.S., Europe, India, China, and Indonesia. Interestingly, the group avoids Russian targets, suggesting possible political motives.
For example, recent attacks targeted the UK’s Royal Mail, the City of Oakland, and automotive retailer Pendragon PLC. Additionally, Lockbit’s ransomware-as-a-service is highly adaptable, capable of double extortion by not only encrypting data but also threatening to publicly release it if ransoms are unpaid.
Lockbit uses a ransomware-as-a-service (RaaS) model, selling its software to other criminals who share the ransom proceeds. Their attacks are typically delivered through social engineering, spear-phishing, or brute-force attacks. Once inside a system, Lockbit autonomously escalates privileges and encrypts files, leaving ransom notes in every folder. Ransom demands range from $100,000 to $10 million.
Despite claiming to operate from various locations, many cybersecurity experts believe Lockbit is Russia-based, as its members are primarily Russian speakers and avoid targeting Russian entities. Lockbit has continuously evolved, with versions 2.0 (Lockbit Red) and 3.0 (Lockbit Black) emerging in 2021 and 2022 to enhance its capabilities and evade detection.
Operation Cronos

Lockbit leak website seized by the authorities
In February 2024, after years of activity, authorities launched Operation Cronos to dismantle Lockbit. On February 19th, law enforcement agencies from the U.S., UK, and EU seized Lockbit’s leak website on the dark web, taking down 34 servers hosting stolen data, decryption keys, and crypto addresses. Two individuals linked to the group were arrested in Poland and Ukraine, and over 200 cryptocurrency wallets were confiscated.
On May 2, 2024, the National Crime Agency (NCA), FBI, and Europol repurposed a seized Lockbit website to disclose insights from the operation, including a list of affiliates and details on Lockbit’s deceptive practices, such as failing to delete stolen data even after ransom payments.
Lockbit’s New Leak Platform
Despite these actions, Lockbit resurfaced quickly. On May 6, 2024, a new Lockbit data leak website appeared on the dark web, accessible only via decryption keys sold by Lockbit for $300.
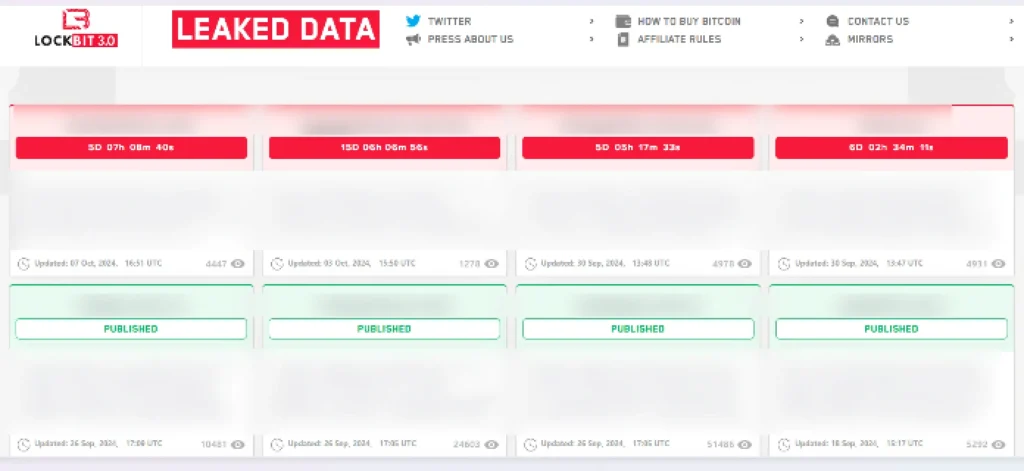
Screenshot exposing Lockbit 3.0 new underground leak website
Links to this site and access keys have been shared on underground forums and social media.
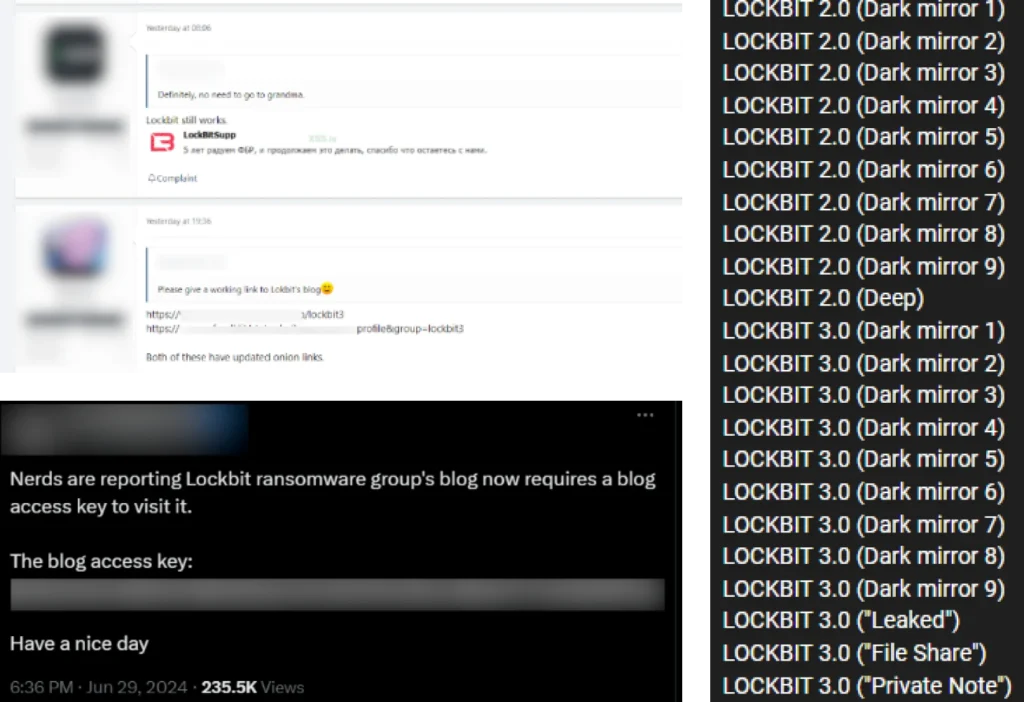
Screenshots exposing underground actors sharing links and access keys to Lockbit 3.0 new leak website
In September 2024, Lockbit also launched a new Telegram channel, where it regularly posts lists of victims and screenshots of stolen data.
Screenshot of Lockbit 3.0 official Telegram channel
In recent months, Lockbit 3.0 has intensified its global attacks. Despite ongoing law enforcement efforts, the group’s swift return and enhanced security measures suggest that the dismantled infrastructure was only a small part of their operation, and they likely have multiple backups to evade further sanctions.
Lockbit 3.0 continues to operate globally, suggesting the infrastructure taken down by authorities was only part of a larger network. Despite ongoing efforts by law enforcement, Lockbit’s swift resurgence and enhanced security measures imply that it holds multiple backups to counter future actions.
Ongoing Threat and Best Practices for Mitigating Ransomware Attacks
In just five years, Lockbit has solidified its position as a major cybercrime threat. Despite extensive efforts by global law enforcement, it remains active and carrying out ransomware attacks globally. To prevent ransomware attacks, organizations should subscribe to a cyber intelligence service such as Outseer’s FraudAction Tier 3 cyber intelligence to stay on top of emerging ransomware group, keep systems updated with security patches, update IT policies as needed and maintain offline backups of critical data. In case of infection, immediately disconnect the affected device from the network to prevent further spread.
Request a consultation to learn more.