Proven fraud protection
Protect your customers, brand, and operations from fraudsters
Safeguard your business with an important defense layer in your in-depth strategy
FraudAction’s proactive threat interception protects brand loyalty and consumer confidence, shielding you from reputational harm and financial losses. It substantially reduces operational costs for banks and financial entities by reducing call center queues and interactions linked to phishing and scams. FraudAction is a key defense layer for any in-depth fraud mitigation strategy.
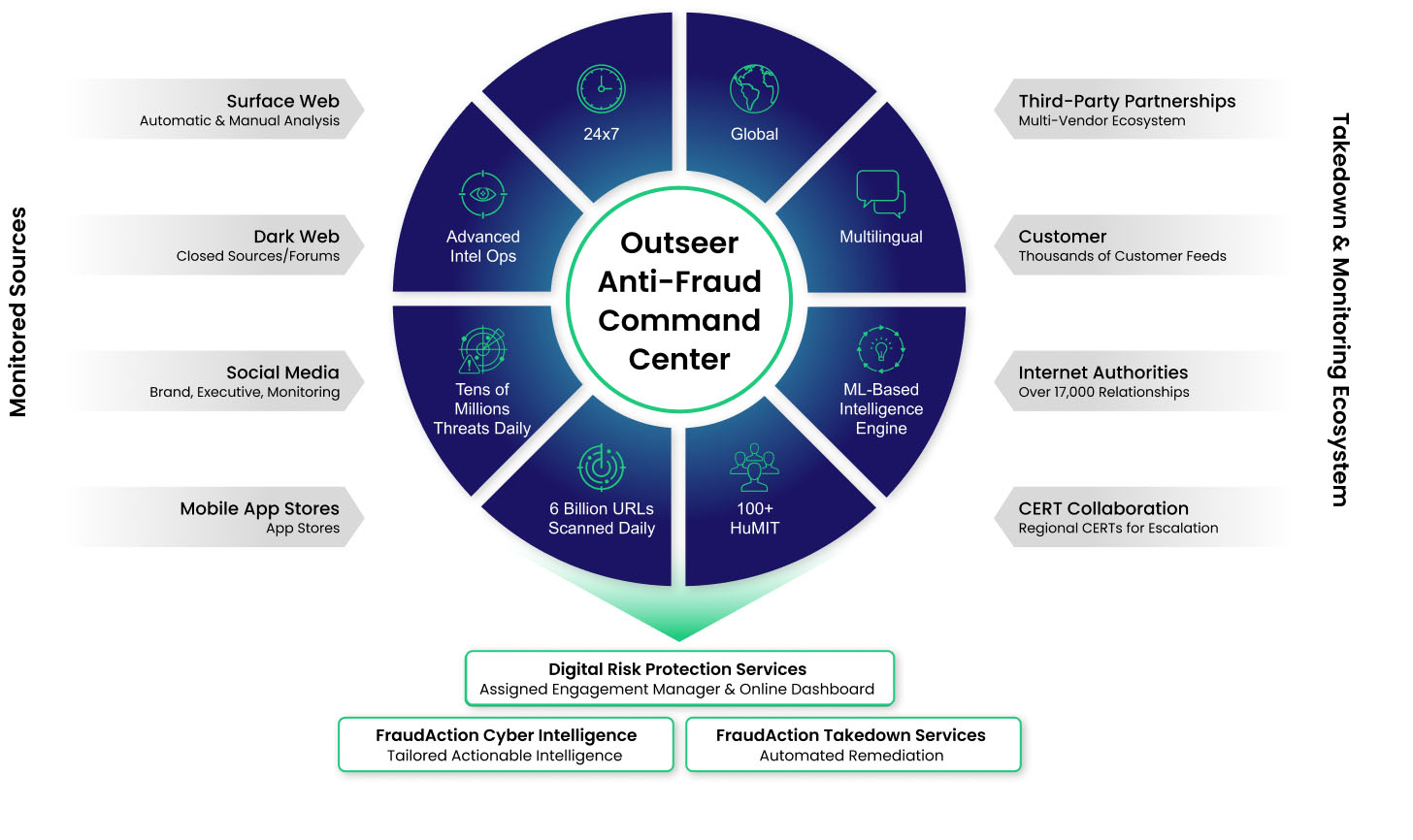
It has been managed by Outseer’s innovative Anti-Fraud Command Center (AFCC) since 2004, which monitors alerts generated by data feeds fueled by our predictive AI-driven intelligence engine. Leveraging expertise and global relationships, it has become the largest and longest-standing fraud operation center in the world.
The AFCC monitors data feeds from the automated predictive AI-driven data intelligence engine. When a threat is detected in the network, the detection is confirmed and the takedown process is swiftly initiated through a far-reaching partner network.

Our team of over 100 highly skilled, multi-lingual intelligence operators monitor tens of millions of potential threats each day. They leverage their many years of underground presence to conduct passive and active monitoring of fraudulent activity across a wide range of communication channels where cybercriminals trade compromised data, Fraud-as-a-Service (FaaS) offerings, tools, and knowledge. Our team conducts deep investigations, cross-reference analysis, and fraudster interrogations.
They have built relationships over 20 years with a global network of over 17,000 ISPs, hosting authorities, international law-enforcement agencies, and other entities to take down these threats and protect millions of end-users around the world. FraudAction Cyberintelligence has a market-leading average takedown turnaround time of under 12 hours.
Assess & manage risks in a single, intuitive dashboard
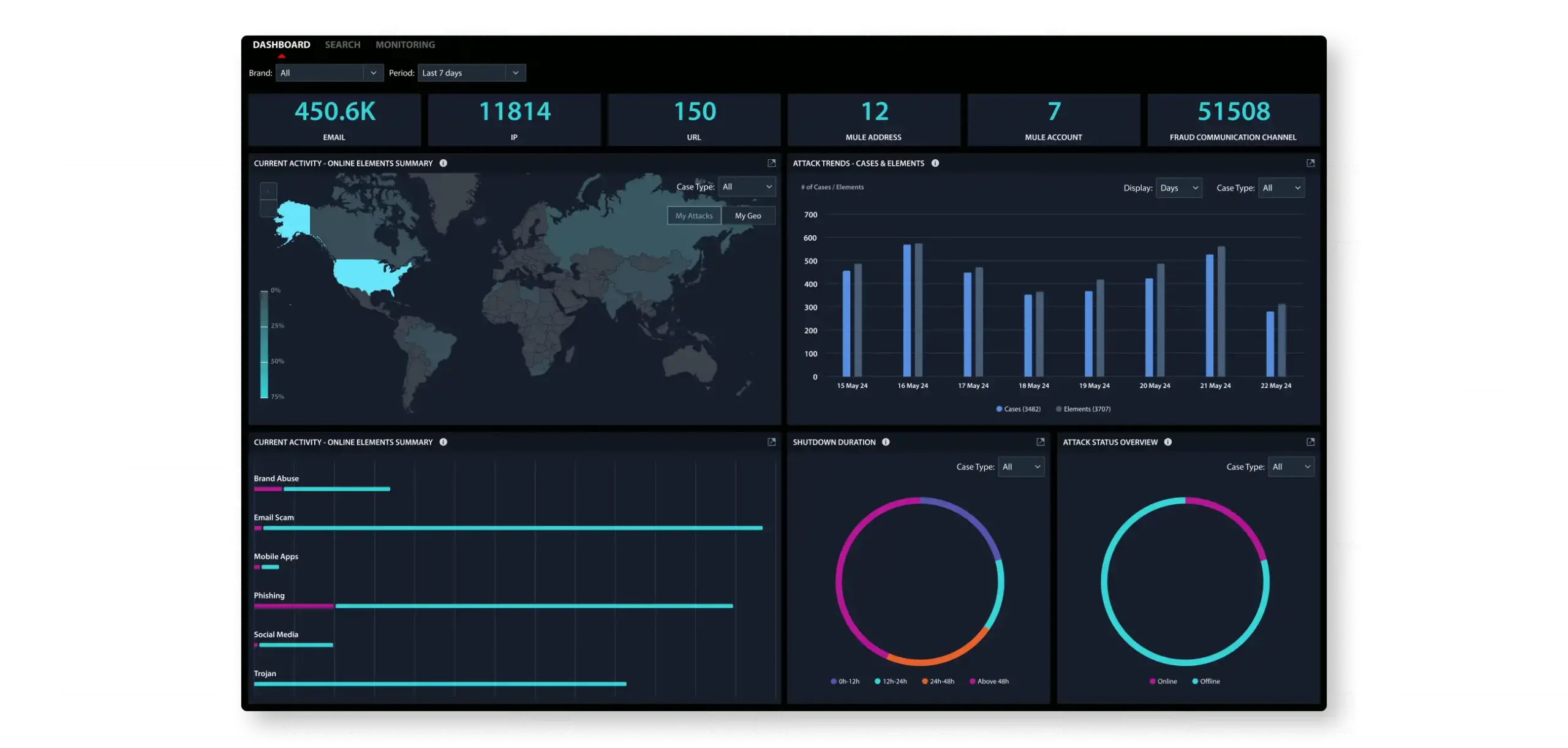
FraudAction 360 Dashboard
You can drill down on the data, view trends through a wide range of graphic widgets, and download the full data set for offline analysis. FraudAction Cyber Intelligence information can also be exported from the dashboard for offline viewing.
FraudAction Cyberintelligence Dashboard API
- View real time status of attacks
- Access and download intelligence feeds
- Use the UI or API to extract the data to other security systems
Automated phishing takedown process
The AFCC also actively monitors app stores for rogue apps and social media phishing. When a threat is found, the global blocking network feeds into major web browser firms such as Google and Microsoft to block consumers from accessing them.
This process is highly automated and our trusted 20+ year relationships allows our blocks to be accepted without delays. Your customers are protected through browser-based blocking within minutes of detected phishing attack.
Detection: Threat detection through Outseer's own monitoring coupled with the efforts our large network of global detection partners.This combination enhances visibility and early detection of phishing attacks before they are launched by cybercriminals.
Validation: The AFCC provides validation of hundreds of millions of suspicious URLs each day by running them through our proprietary risk engine and scoring them based on multiple parameters. URLs above the risk threshold are sent to analysts for manual validation.
Blocking: Immediately after a threat is validated, the AFCC acts to distribute phishing URLs to our blocking partners—covering Chrome, Edge, Firefox, and Safari. Our global blocking network feeds confirmed phishing URLs into major web browser firms to block consumer access to the sites. Blocking is typically implemented within minutes of detection, quickly protecting your customers from potential phishing.
Experience FraudAction for Yourself
Request a TrialReal-time cyber threat and brand monitoring
A Comprehensive Threat Takedown Service
Dark Web Monitoring & Intelligence
Explore our partner ecosystem
To discover an Outseer FraudAction partner that can support your needs within your region, please request a consultation and provide us with details of your requirements.