Ensuring security and compliance in Card-not-present (CNP) payments remains paramount. Among the arsenal of tools and protocols aimed at fortifying payment integrity, EMVCo is the global standard that sits alongside card schemes, regional and local regulations. Yet, comprehending its complexities and staying abreast of compliance changes presents a challenge for stakeholders across the payment ecosystem.
As CNP and e-commerce transactions continue their exponential rise, so does the looming threat of fraud. Projections depict a staggering surge in total payment card volume, paralleled by an alarming increase in fraudulent activities. Regions such as North America, Latin America, and Asia Pacific grapple with significant fraud challenges, underscoring the urgent need for financial institutions to adopt EMV® 3-D Secure and similar regulations such as Strong Customer Authentication (SCA).
In this context, let’s explore EMVCo in detail, understanding its mechanisms and intricacies. We’ll also examine Outseer’s role in ensuring standard compliance, its adept adaptation to regional nuances like SCA regulations, and its facilitation of local compliance intricacies, such as Sweden’s Bank ID.
EMVCo’s Pivotal Role in Setting Industry Standards for Global Compliance
EMVCo, a consortium owned by major payment networks, spearheads the establishment of industry standards for payment security and interoperability. By adhering to EMV specifications, stakeholders ensure compatibility with global payment standards, fostering a secure and cohesive ecosystem.
EMV® 3-D Secure encompasses a multi-faceted approach involving consumers, merchants, card networks, and issuers. At its core, it seeks to authenticate cardholders during online transactions, thereby reducing the risk of fraud. Understanding the roles of each stakeholder is crucial to comprehending the framework’s efficacy.
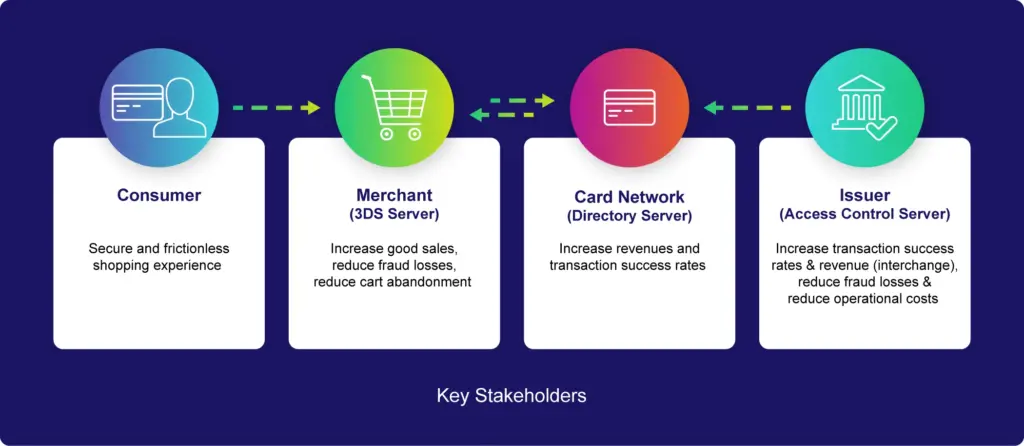
- Consumer: EMV® 3-D Secure prompts consumers to authenticate themselves using multiple factors, such as passwords, biometric data, or tokens, ensuring the legitimacy of the transaction.
- Merchant (3DS): Merchants integrate 3-D Secure protocols into their checkout processes, enabling secure authentication and mitigating the risk of unauthorized transactions.
- Card Network (Directory Server): Card networks maintain directory servers that facilitate the authentication process by providing necessary information to merchants and issuers.
- Issuer (Access Control Server): Issuers operate access control servers to validate transaction requests, leveraging advanced algorithms and data analytics to detect and prevent fraudulent activities.
Credit Card Network Schemes for Global Compliance

Alignment with major credit card network schemes is essential for ensuring global compliance. This alignment involves adherence to standards and integration with network protocols to ensure global reach.
Here’s how a card scheme facilitates transactions: initially, when a customer makes a purchase using their payment card, whether in-store or online, the transaction is initiated. Subsequently, the payment details are communicated to the merchant’s bank. Then, the bank forwards an authorization request to the pertinent card scheme, such as Visa or Mastercard. The card scheme then routes this request to the customer’s bank for fund verification and card validity confirmation. Based on this assessment, the transaction is either approved or denied. If approved, the payment is processed through the card scheme and deposited into the merchant’s account. Scheme owners commonly enforce compliance requirements on banks and technology providers to utilize their card schemes, thereby ensuring global standards are upheld.
By embracing and adhering to scheme mandates through Outseer support and expertise, card issuers mitigate the complexities of cross-border transactions, paving the way for frictionless commerce while fortifying defenses against fraud.
Regional Regulation & Compliance: Strong Customer Authentication
Navigating regional compliance requirements, particularly in the realm of card not present (CNP) payments, poses a challenge for stakeholders globally. The European Union’s Revised Payment Services Directive (PSD2) stands out as a prime example of regulatory evolution, with its SCA mandate significantly impacting CNP transactions.
Implementing SCA-compliant authentication measures is crucial not only for meeting regulatory obligations but also for enhancing security in online transactions while simultaneously minimizing customer friction. In regions like the EU, where SCA is enforced, successful compliance strategies highlight the importance of partnering with 3-D Secure ACS providers. Such partnerships facilitate the adoption of robust authentication mechanisms, ensuring compliance with regulatory standards while optimizing operational efficiency for merchants and financial institutions alike.
Regional regulation compliance often extends beyond the originating region, with numerous regions worldwide implementing their own frameworks and adaptations. This global trend reflects the diverse regulatory environments and the need for tailored approaches to address specific regional requirements and challenges. For instance, Australia has developed its regulatory equivalent of SCA to enhance payment security.
These adaptations highlight the significance of comprehending and navigating the complexities of compliance frameworks in pivotal regions. Outseer’s swift support for major customers in areas like EMEA/UK concerning new regulatory requirements facilitates fast and easy adaptation and compliance, ensuring seamless support for customers in other regions when similar regulations are implemented.
Local Compliance Intricacies: Sweden’s BankID

BankID is the mandatory electronic identification method in Sweden, playing a crucial role in authorizing payments and transfers securely. However, its adoption has also made it a target for fraudsters who exploit its popularity and trust among users.
Common frauds associated with BankID include fake bank support, scams via companies or friend on social media and ID theft via security token. These fake support and scams, trick individuals into disclosing their BankID credentials, and identity theft, where fraudsters use stolen BankID information to conduct unauthorized transactions.
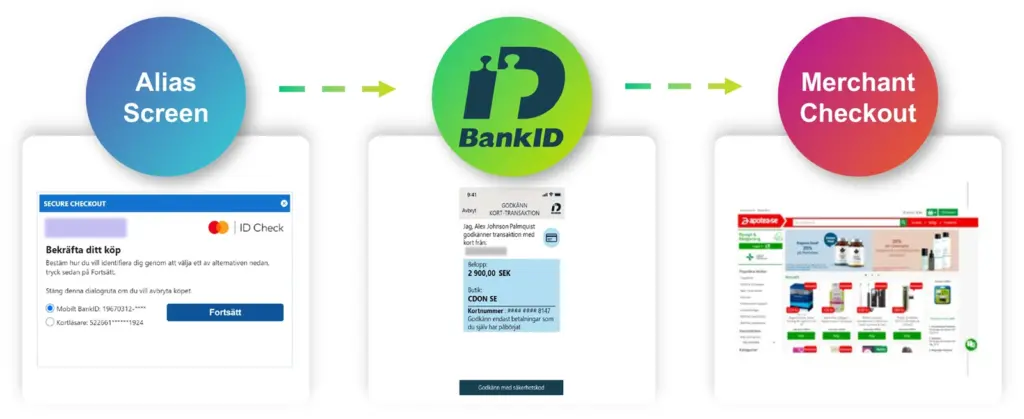
To combat this, Outseer through its 3-D Secure solution introduced QR challenge flows for online transactions. The QR code feature is particularly beneficial when consumers access an online merchant’s platform using a device different from the one where they have their Mobile BankID stored, such as a personal computer, tablet, or public device. This additional layer of security ensures that transactions remain protected, even across various devices, strengthening consumer confidence in online purchases.
Outseer: Leading the Way in Regulation & Compliance Expertise
When comes to global, regional and local regulations, Outseer’s 3-D Secure solution provides customized and best practice approaches to compliance and risk mitigation.
With knowledge and expertise for compliance at both global and regional levels, Outseer help financial institutions swiftly adapt to not only global regulations but also pivot to comply with regional and local regulations as they evolve across different regions. Features like QR challenge flows not only enhance security but also cater to diverse consumer preferences and adhere to localized regulations.
This adaptability ensures that institutions remain compliant and competitive in the dynamic regulatory environment.
For more insights from our experts, watch the webinar: 3-D Secure: Navigating Compliance Changes