Author: Noya Garty, Fraud Action Intelligence Tech Lead
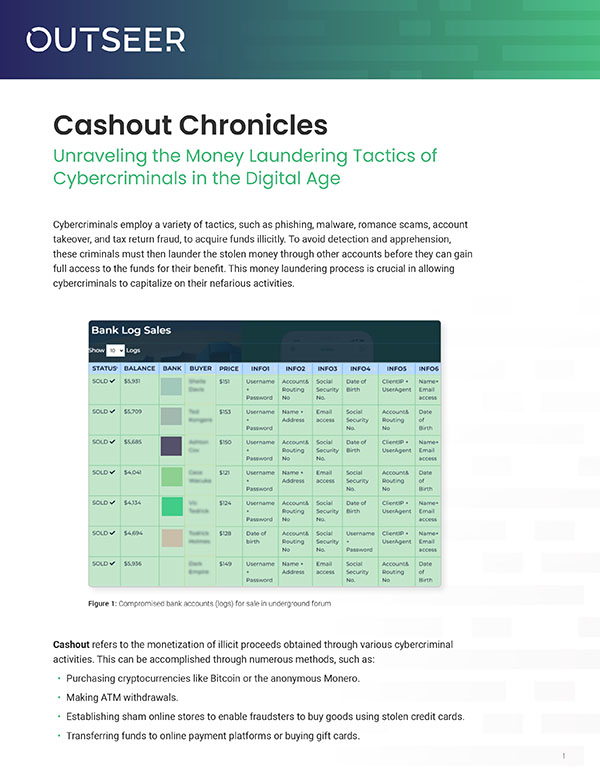
Cybercriminals employ a variety of tactics, such as phishing, malware, romance scams, account takeover, and tax return fraud, to acquire funds illicitly. To avoid detection and apprehension, these criminals must then launder the stolen money through other accounts before they can gain full access to the funds for their benefit. This money laundering process is crucial in allowing cybercriminals to capitalize on their nefarious activities.
Get this report to learn how fraudsters are drawn to real-time payment apps for the same reasons as legitimate users: usability and transfer speed. Consequently, compromised accounts connected to these apps are particularly attractive to criminals, who can effortlessly move stolen funds to mule accounts registered with instant payment services.
Learn how to identify and monitor such mule accounts, helping flag illicit activity now.