Over the past few years, Outseer has observed a significant uptick in authorised push payments, mule accounts, and account takeovers within the industry. This has been dramatically influenced thanks to the changes in our own personal lives and spending but also the ecosystem itself. Fraudsters have latched onto these changes by focusing their attacks more on the emotional side of an individual, thus creating a challenge for banks and merchants to prevent such cases from happening.
To fully understand authorised push payments and mule account scams we need to go back to the start, where the fraud begins. These types of attacks rely on the fraudster knowing personal information about your customers. To do this they will need to perform either a phishing attack or buy/obtain the information from elicit sources like the dark web.
Fraudsters mainly employ three data-gathering techniques:
- Phishing – sending deceptive emails that appear to originate from a trusted/genuine source to influence or gain personal data.
- Vishing – eliciting information or attempting to influence action via the telephone, may include other tools such as ‘phone spoofing’ technology.
- Impersonation – Posing as someone else to obtain information or access to a specific person, company, or computer system.
Once the fraudster has obtained personal information about your customer, it becomes easier for them to forge connections, enhancing their credibility. For example, a fraudster who calls a customer by their first name and confirms whom they bank with, and other personal information will always seem more genuine than a cold call, where the fraudster has nothing to connect with the customer.
Below summaries how the data is gathered:
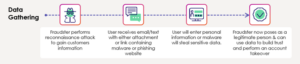
As indicated by Datos Insights, (formerly Aite-Novarica), research Faster Payments, Faster Fraud report (published on May 2023), the consumer is the weakest link as fraudsters have developed a tried-and-true playbook and have replicated this attack vector across multiple geographies. The challenges with stopping fraudsters from obtaining such personal information rely heavily on customers being vigilant and educated about potential threats. Regrettably, educational resources often become available too late—usually when the fraudster is already in conversation with the client other challenges in detecting social engineering include:
- Expansive attack vectors.
- There’s no need for advanced hacking techniques.
- Social Engineering is now available on a “for hire” basis
- Exploitation of human emotions such as fear, urgency, and greed.
- General human fallibility.
- Inadequate social engineering training.
- Lack of data.
- Over-reliance on trusted partner.
All of these combined allow fraudsters to be successful with social engineering scams.
Once the fraudster has obtained the personal identifiable information (PII) from the customer this is where they will use it to exploit funds from the customer’s accounts. This is normally done in 3 ways:
| Mule account we know (age of account/transactional history) |
Mule account we don’t know (a newly created account) |
Authorised push payment |
|---|---|---|
|
|
|
As the threat landscape evolves so does Outseer’s platform, as there is no silver bullet defense for scams, we recommend a multi-layered approach.
The first layer in your scam mitigation strategy should be to limit the credentials and PII of your customers that fraudsters can access. Outseer FraudAction service can help you do just that.
The second phase in your scam mitigation journey is tracking scams. Today, many FIs do not track this type of fraud but you can’t fight what you don’t track so for a start it is recommended that FIs will tag these types of attacks so they can better analyse their characteristics and mitigate them more efficiently. For this purpose, Outseer Fraud Manager’s July 2023 release included new capabilities to its case management application, you can tag a case as a “scam” and then filter based on this tag. This can help you characterize the attributes of a scam attack and fine-tune your policies to more effectively counter these attacks.
Genuine user behaviour often disguises fraudulent activities. As part of Outseer’s Fraud Manager we decided to enable our customers to introduce smart friction and ask contextual questions to their users about how they feel, do they feel confident, and whether they are receiving advice or guidance over the phone. Below is an example of how we can help your organisation protect your customers from making a costly mistake in the payment transfer flow:
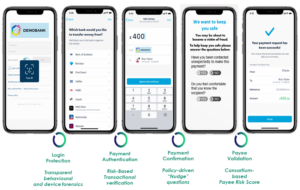
Another crucial layer involves sharing fraud data/signals across organisations. Outseer Global Data Network helps our customers fight fraud as a community. When one of the community members marks a transaction as fraudulent the transaction data is shared across our network.
To help our customers apply their own business risk acceptance the Outseer policy manager has specific rules that focus on such scams. Examples of these could be an increase in payment velocity, the sum of payments received from a specific payee and other anomaly detection capabilities. Outseer has designed the solution to be as flexible as possible to cater to our customer’s varying business needs.
As fraudsters continue to evolve the way they manipulate customers, we at Outseer are committed to evolving our solutions to address these challenges. We believe our ongoing development efforts will empower our customers/you to say one stead ahead of fraudsters.
Discover more about scams in our webinar titled, From Scam to Cash Out: Follow the Money Trail.